How Can an Adversary Use Information to Target You? The Cybersecurity Threat Explained! Cyber attacks faced by different departments information security risk
If you are searching about Solved: How can an adversary use information available in public you've came to the right web. We have 25 Images about Solved: How can an adversary use information available in public like Solved: How can an adversary use information available in public, Understanding Known Adversary Tactics and Techniques and also Adversary Targeting - Cyber and Threat Intelligence Webinar | Treadsto. Here you go:
Solved: How Can An Adversary Use Information Available In Public
What We Can Do About Cyber Attacks That Are On The Rise - - Studocu
 www.studocu.com
www.studocu.com
How To Protect The Enterprise From Cybersecurity Attack
 www.gartner.com
www.gartner.com
How Well Are You Protected Against Cyber Threats? Take Our 5-Minute
 www.visory.net
www.visory.net
A Four Step Approach To Improve Security Threat Response - TechB2BShoot
 techb2bshoot.com
techb2bshoot.com
Threats And Technology: How Attacks Adapt Best Practice, Cyber Security
 www.pinterest.com
www.pinterest.com
Solved A is When An Adversary Attempts To Achieve User | Chegg.com
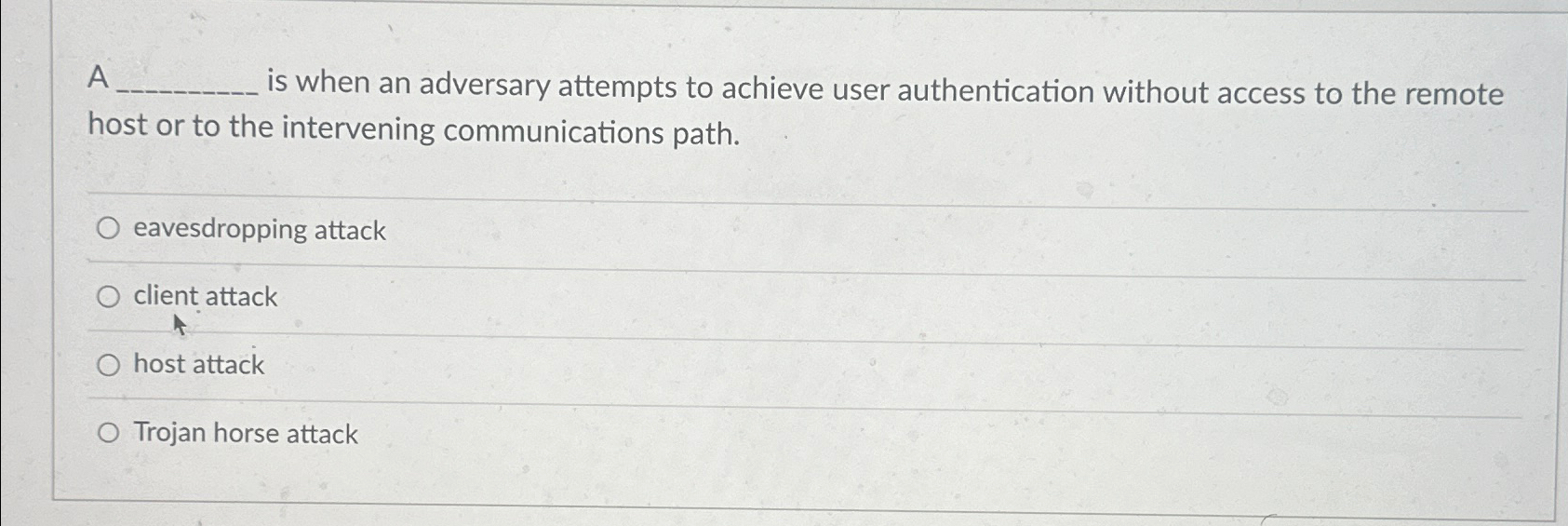 www.chegg.com
www.chegg.com
Adversary-focused Cybersecurity | Deloitte Insights
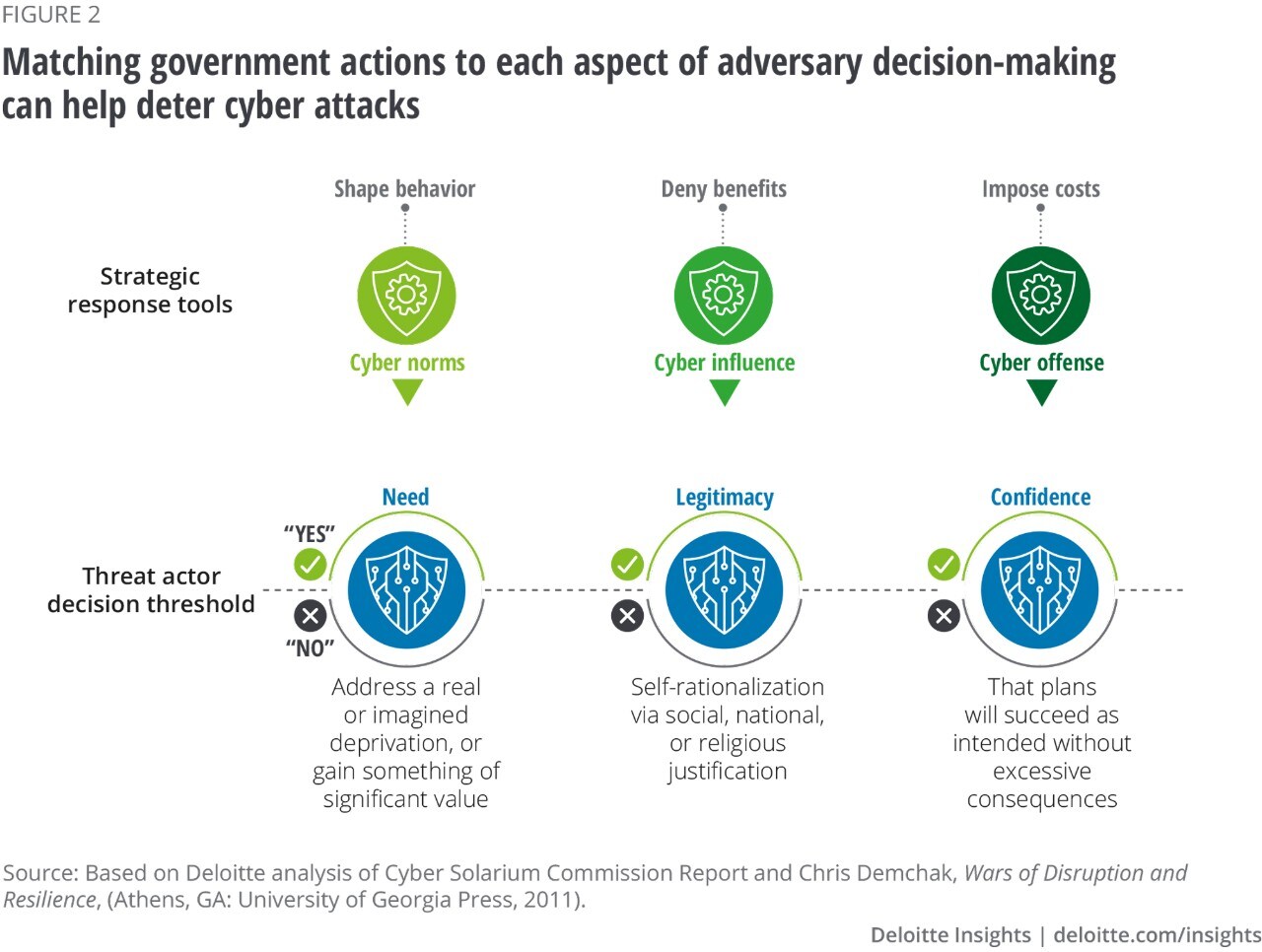 www2.deloitte.com
www2.deloitte.com
adversary deloitte cybersecurity
What Is Cybersecurity Threat.docx - What Is Cybersecurity Threat? A
 www.coursehero.com
www.coursehero.com
Cyber Security Attack Target And Defense Measures Ppt Infographic
 www.slidegeeks.com
www.slidegeeks.com
Threat Modeling : From Software Security To Cyber Risk Management
 www.conquer-your-risk.com
www.conquer-your-risk.com
How To Identify The Motive Behind Your Cyber Threat Adversary
 www.netsecurity.com
www.netsecurity.com
Understanding Known Adversary Tactics And Techniques
 www.threatq.com
www.threatq.com
Cyber Attacks Faced By Different Departments Information Security Risk
 www.slidegeeks.com
www.slidegeeks.com
Adversary Targeting - Cyber And Threat Intelligence Webinar | Treadsto
adversary targeting threat matrices
How Well Do You Know Your Cyber Threats And Are You Protected
 www.netsecurity.com
www.netsecurity.com
Learning From Your Adversary: An Inside Analysis Of The Latest Cyber
 www.brighttalk.com
www.brighttalk.com
Dealing With Cyber Attacks–Steps You Need To Know | NIST
 www.nist.gov
www.nist.gov
steps nist cyber cybersecurity framework attacks dealing handle take can need know gov response step rocks focus big risk manufacturing
(PDF) Understanding And Investigating Adversary Threats And
 www.researchgate.net
www.researchgate.net
[PDF] The Role Of The Adversary Model In Applied Security Research
![[PDF] The Role of the Adversary Model in Applied Security Research](https://d3i71xaburhd42.cloudfront.net/d9bf39f218d58404d157df832ab69f516893eaff/13-Table1-1.png) www.semanticscholar.org
www.semanticscholar.org
Strategic Impact Of Cyberattacks On The Adversary | Download Scientific
 www.researchgate.net
www.researchgate.net
Exploring Cyber Attack Types: Understanding The Threat Landscape | PDF
 www.slideshare.net
www.slideshare.net
HOW TO Avoid Cybersecurity Threat Chapter 2 - HOW TO AVOID
 www.studocu.com
www.studocu.com
Cyberopsalliance.com | - Ppt Download
 slideplayer.com
slideplayer.com
Solved: How Can An Adversary Use Information Available In Public
Threats and technology: how attacks adapt best practice, cyber security. Steps nist cyber cybersecurity framework attacks dealing handle take can need know gov response step rocks focus big risk manufacturing. Adversary-focused cybersecurity